
We believe in securely connecting everything by enabling users to build private networks within the internet that only they can see. We provide zero trust IT/OT networking as a service.
Language
English
日本
Secure Shell (SSH) is a protocol for secure connections to remote computers or servers. The protocol encrypts communication so you run commands, transfer files, and manage systems safely over the internet.
Developers, system admins, and IoT engineers use SSH daily to:
Port forwarding is a networking technique allowing external devices to connect to a service inside a private network.
For example:
Common uses of port forwarding with SSH include:
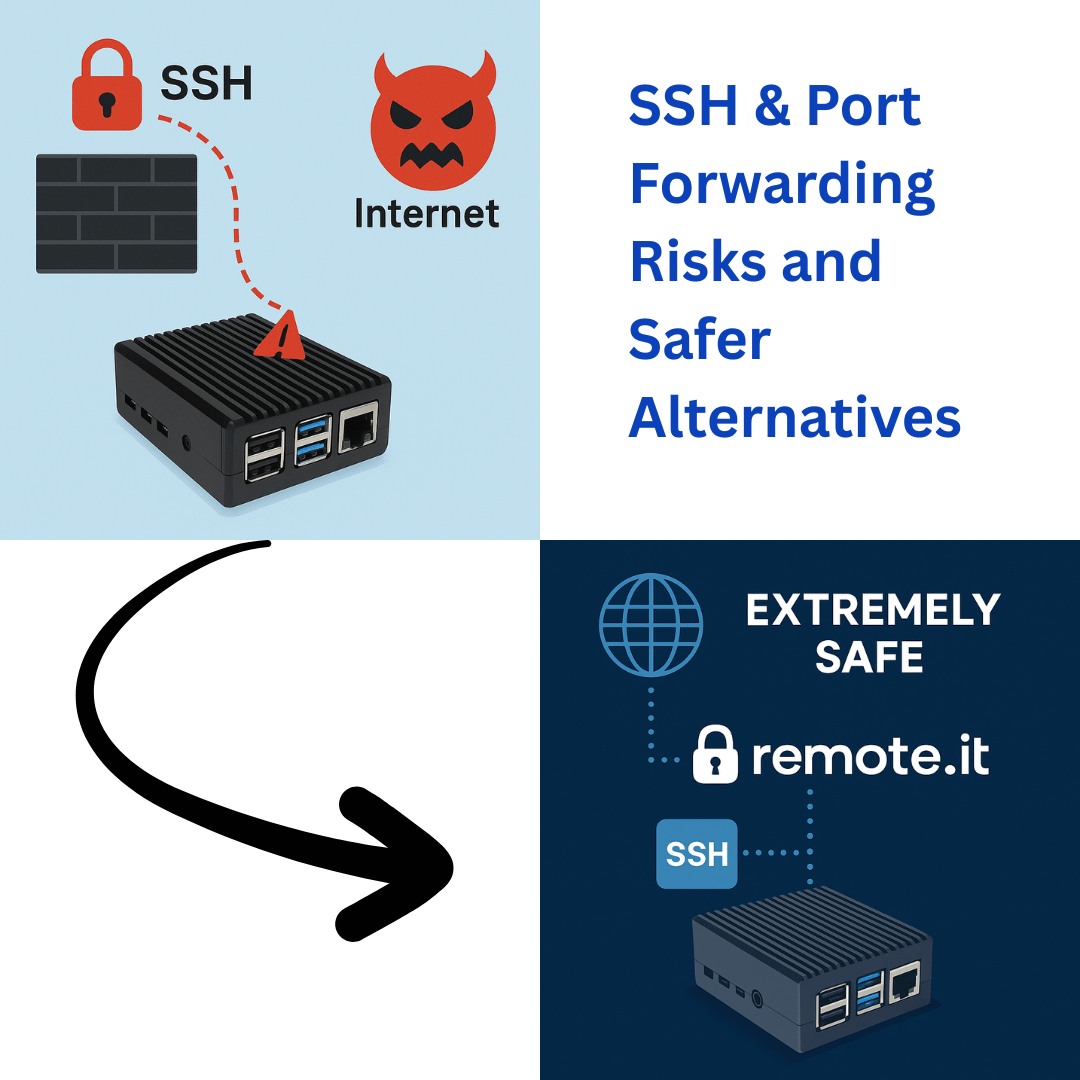
The combination allows a user anywhere in the world to connect directly to a specific device on a private network. The approach is simple, well-documented, and works with almost any internet-connected device.
But the method comes with serious trade-offs.
Instead of opening ports and exposing your network, Remote.It connects you to devices securely without changing any firewall settings.
How Remote.It Works:
Example: With port forwarding, you might open port 22 on your router to SSH into a Raspberry Pi. With Remote.It, the Pi stays hidden, and you connect to its SSH service securely through the Remote.It app or CLI: no public exposure, no router changes.
SSH is a solid tool, but combining it with port forwarding creates unnecessary risk and complexity. Remote.It gives you the same remote access (and more) without the security trade-offs.
Whether you’re managing a single device at home or an entire fleet of servers in the cloud, Remote.It keeps you connected, invisible, and secure.
Start using Remote.It for SSH today