
We believe in securely connecting everything by enabling users to build private networks within the internet that only they can see. We provide zero trust IT/OT networking as a service.
Language
English
日本

In today’s threat landscape, the most dangerous network connections are the ones too open, too broad, and too visible.
Yet traditional tools (VPNs, firewalls, and ACLs) revolve around IP addresses and port ranges. This creates a false sense of control while leaving excessive access paths exposed.
Remote.it flips this model on its head.
Instead of managing access to networks, Remote.it grants access to services: specific, named processes running on devices.
And in doing so, delivers invisible but essential security, by design.
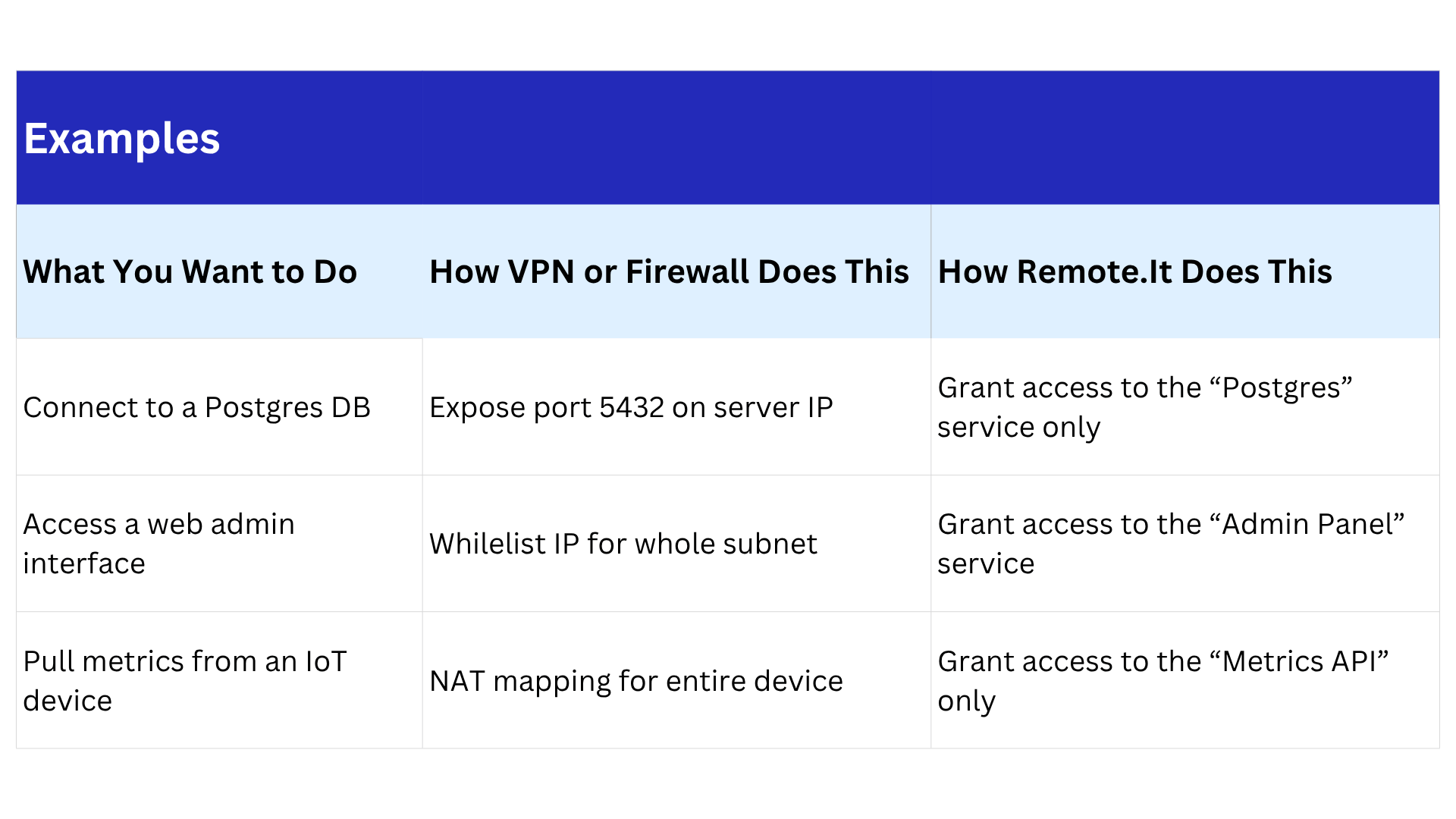
IP addresses are blunt tools. A developer needs access to a database on port 5432, but if you open the server’s IP, you risk exposing everything else: SSH, file systems, internal APIs.
Every open IP is a potential attack surface.
Even when you firewall ports, common scanning tools like Shodan and Nmap find them. Worse, organizations often reuse public IPs across services and environments. What starts as convenience becomes an unpredictable risk.
Remote.it eliminates the concept of exposed IPs altogether.
Instead, you define services (like a database, a specific web application, or a local API) and grant access only to those. Remote.it’s architecture routes connections directly to the service, not to the device, subnet, or network.
This is true least-privileged access.
Zero Trust isn’t a product. The principle:
Remote.it supports Zero Trust by enforcing:
Connections only exist when you grant, scope, and verify them. And even then, Remote.it routes them through its private, encrypted relay (not exposed on the internet).
Your developers don’t need to worry about static IPs, firewall rules, or VPN clients.
Your security team doesn’t need to audit network routes or hunt for misconfigured ports.
Remote.it operates behind the scenes, embedding service-level connectivity directly into your workflow through CLI, SDKs, or GUI. Seamless for users but precise and auditable for admins.
With Remote.it:
Not Zero Trust compliant.
Zero Friction.
See what invisible connectivity looks like.
Explore Remote.it and start connecting with confidence, because the best security is the one you never see, but always trust.
A: Instead of opening a full device or network to access something like a database, Remote.it lets you define and expose only the specific service (e.g., PostgreSQL on port 5432). Users or applications connect directly to the service without gaining access to the underlying OS, device, or subnet.
A: Zero Trust means granting the least amount of access necessary, verifying every connection, and assuming no default trust. Remote.it enforces this by:
A: No. Remote.it services never expose themselves to the public internet. We open no ports, provide no IP addresses to scan, and ensure nothing appears in tools like Shodan. Your infrastructure stays invisible by design.
A: VPNs grant network-level access (often more than what’s needed) and introduce lateral movement risks. Remote.it only connects users to the service they’re authorized for. No broad access. No subnet exposure. No management overhead.